Read Post
WGR614v10 and WNR1000v3 Cross-Flashing Firmware Update - part 1
Our SOHO DSL internet connection is pretty stable, PPPoE through Netgear WGR614v10, covering almost 200 square meters of the area with concrete walls. Everyone was happy, no connection dropping, until recently. I needed to share the internet connection over Wifi to another wireless router, but it didn’t work no matter what. When I swapped both routers, it worked. But that is not the point. The point is, no matter what router installed as internet gateway, it should be able to share its internet connection. So I guess, it is time for this WGR614v10 to get a firmware upgrade.

I wanted to flash WGR614v10 with OpenWrt. Unfortunately, it is not yet supported, maybe next time. But I found an intriguing blog posts, here and here, saying that WGR614v10 can be updated with WNR1000v3 firmware. Interesting! Both routers might have a similar configuration in order to make it work! Googling around for hardware comparison, it turned out that both routers look so identical. According to Wikidev WGR614v10 and Wikidev WNR1000v3, both have the same type of Broadcom chip. So, why WGR614v10 was marketed as Wireless-G and the latter as Wireless-N? Below are pictures showing board layout of WGR614v10(left) and WNR1000v3(right).
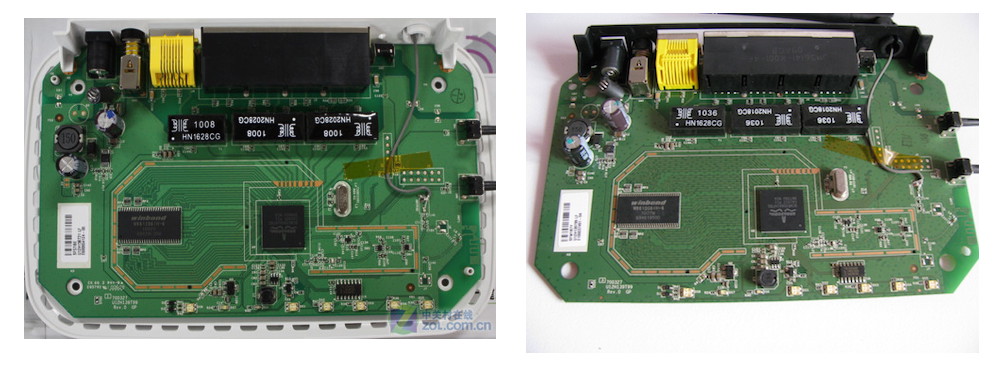
What is more interesting about old Netgear routers, is that there is an unprotected backdoor telnet console. But it needs to be activated, which is described here in detail. There are a lot of build platforms and versions for different Netgear routers, for mine I used this telnetenable. We need telnet access to replace WGR614v10 board ID with the one of WNR1000v3. This is actually to fool WGR614v10 to think that it is WNR1000v3 to allow WNR1000v3 firmware upload. Below you may find commands over telnet to burn the board ID. Parameters for telnetenable is router’s IP address, MAC address, username, and password. The U12H139T00_NETGEAR is WNR1000v3 board ID.
NetgearTelnetEnable nodino$./telnetenable 10.0.0.1 C03F0E56945C Gearguy Geardog
NetgearTelnetEnable nodino$ telnet 10.0.0.1
Trying 10.0.0.1...
Connected to 10.0.0.1.
Escape character is '^]'.
BusyBox v0.60.0 (2010.07.24-08:33+0000) Built-in shell (msh)
Enter 'help' for a list of built-in commands.
# burnboardid U12H139T00_NETGEAR
Board ID - U12H139T00_NETGEAR
BurnBoardId OK
# Now that the hardware is faked to think that it is WNR1000v3, it is time to fire the web interface and update the firmware. DO NOT UPDATE FIRMWARE OVER WIRELESS CONNECTION. DO IT THROUGH AN ETHERNET CABLE. DO IT AT YOUR OWN RISK! THERE IS NO WARRANTY THIS METHOD WILL WORK FOR YOU. YOU'VE BEEN WARNED! Our Wifi router’s address is 10.0.0.1, yours might be different. Download WNR1000v3 firmware from Netgear Download Center.
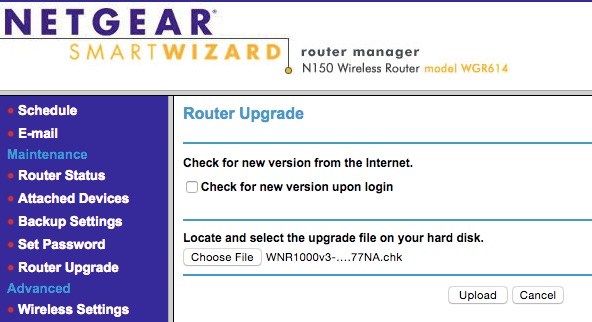
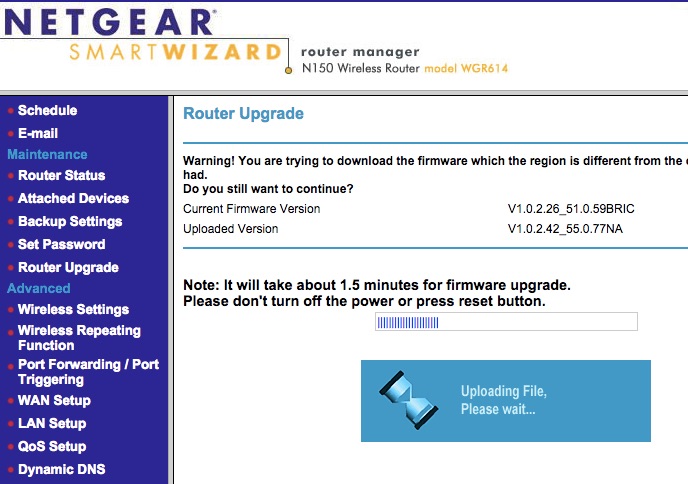
Don’t turn off the device until the process is done. Don’t interrupt the upgrade process or you might brick your device. After it is done, voila! The new look of your WGR614v10 is now WNR1000v3!
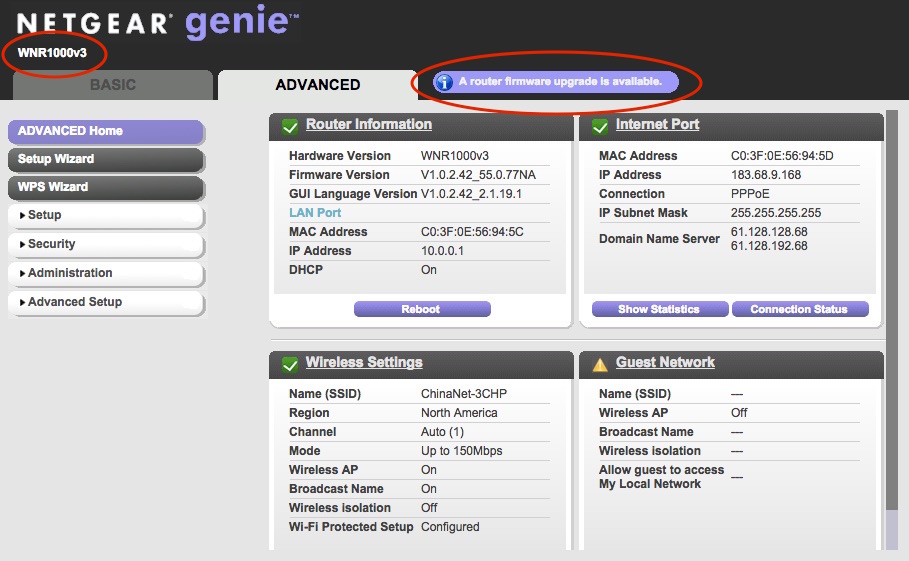
Wait a minute! There is even more! It seems that there is a new firmware already from Netgear repository. Let’s update it one more time. This the good thing of having WNR1003v3 firmware with longer support from Netgear. At least we need it until OpenWrt is fully supported on WGR614v10 or WNR1000v3.
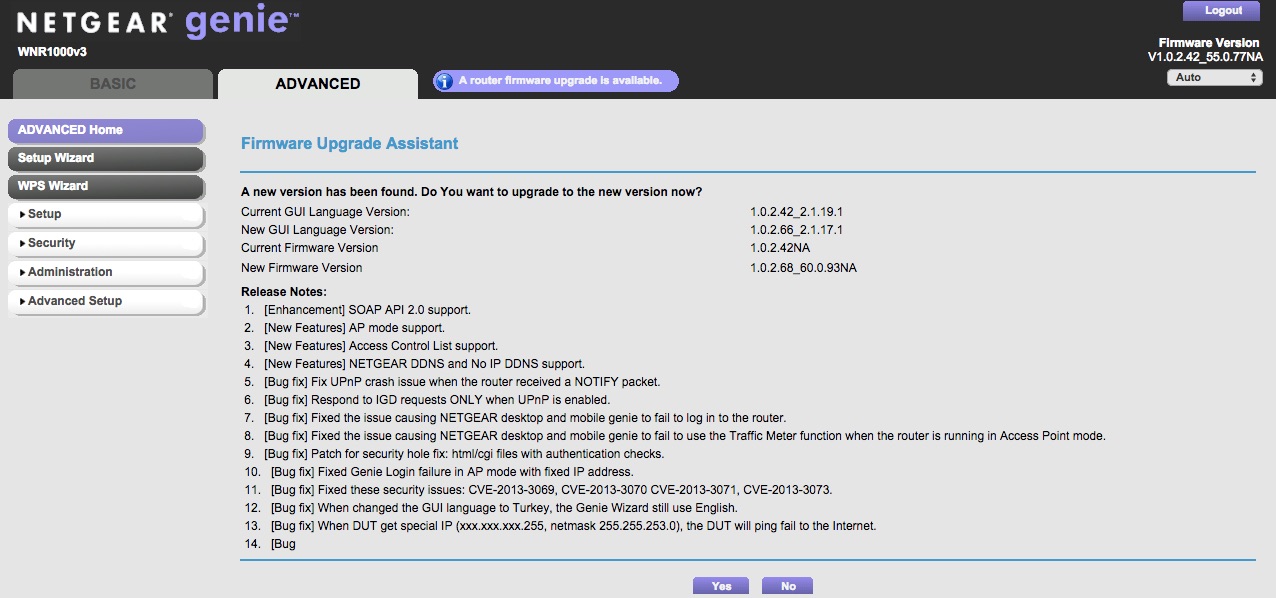
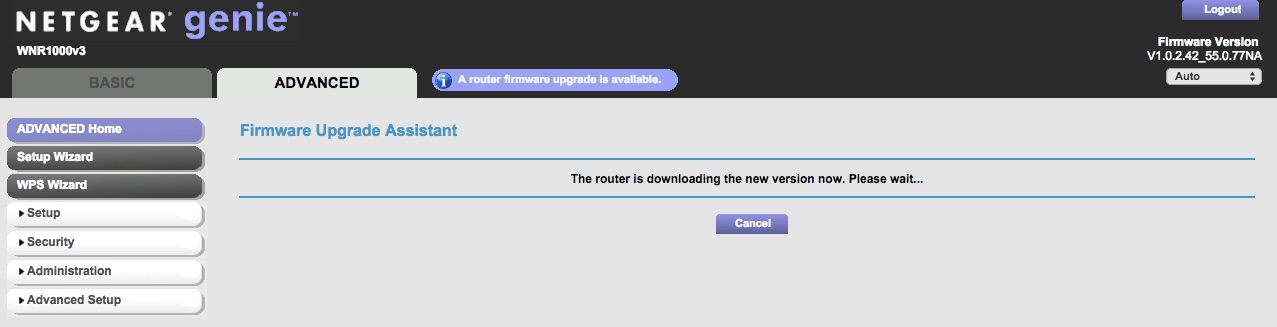
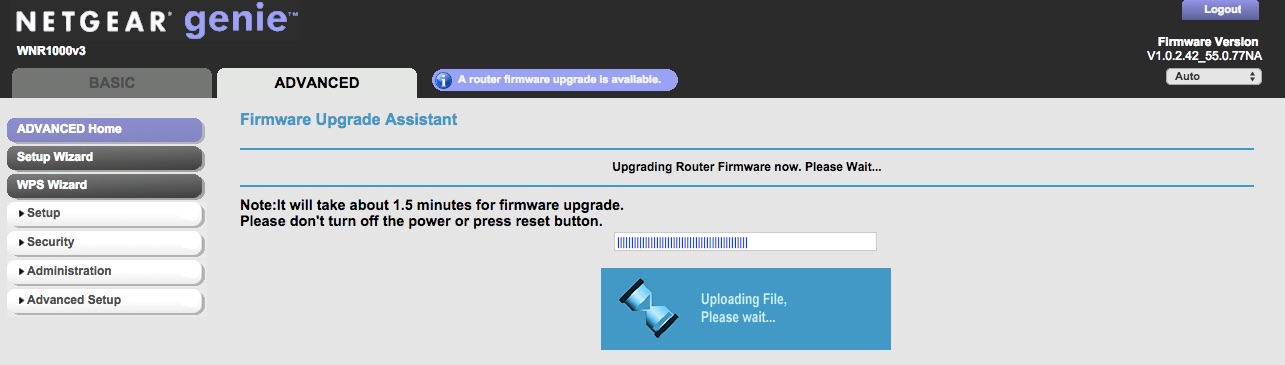
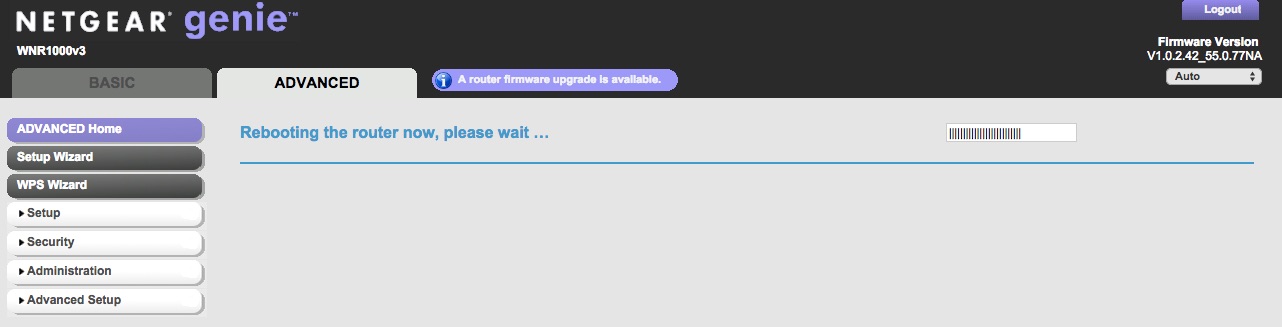
This is the final look of WNR1000v3 with nicer background and theme.
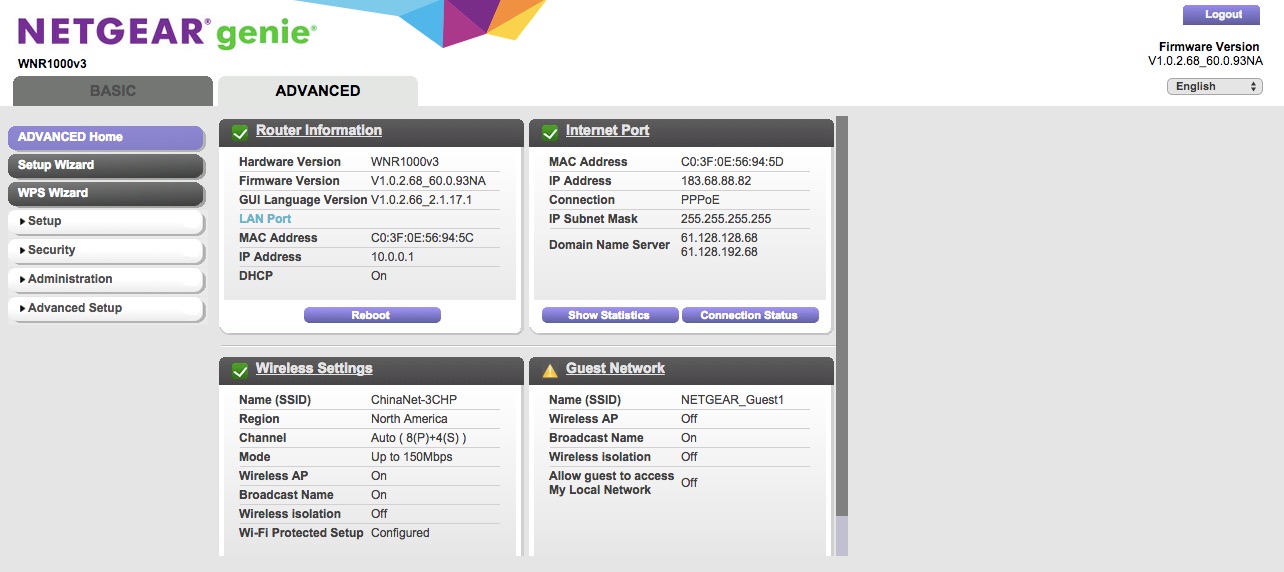
Is there another way to do it without backdoor telnet? Let’s say you have already upgraded your WGR614v10 with the latest firmware from Netgear Download Center, the backdoor access might not be there anymore. Fortunately, there is another way! Follow Cross-Flashing Part 2 to see how.
