Read Post
HG8245 - Root Password to Reveal Hidden Menu
I managed to hook a USB to serial cable to HG8245 in here to get access to console. Then, I stumbled across a blog post explaining how to gain root access. This access to root can be used to revealed a hidden menu within the web interface.
This is how to get the telecomadmin’s password:
WAP(Dopra Linux) # grep telecomadmin /mnt/jffs2/hw_ctree.xml
<X_HW_WebUserInfoInstance InstanceID="2" UserName="telecomadmin" Password="telecomadmin35198845" UserLevel="0" Enable="1"/>
WAP(Dopra Linux) # This is how to get the useradmin’s password:
WAP(Dopra Linux) # grep useradmin /mnt/jffs2/hw_ctree.xml
<X_HW_WebUserInfoInstance InstanceID="1" UserName="useradmin" Password="ssn2q" UserLevel="1" Enable="1"/>
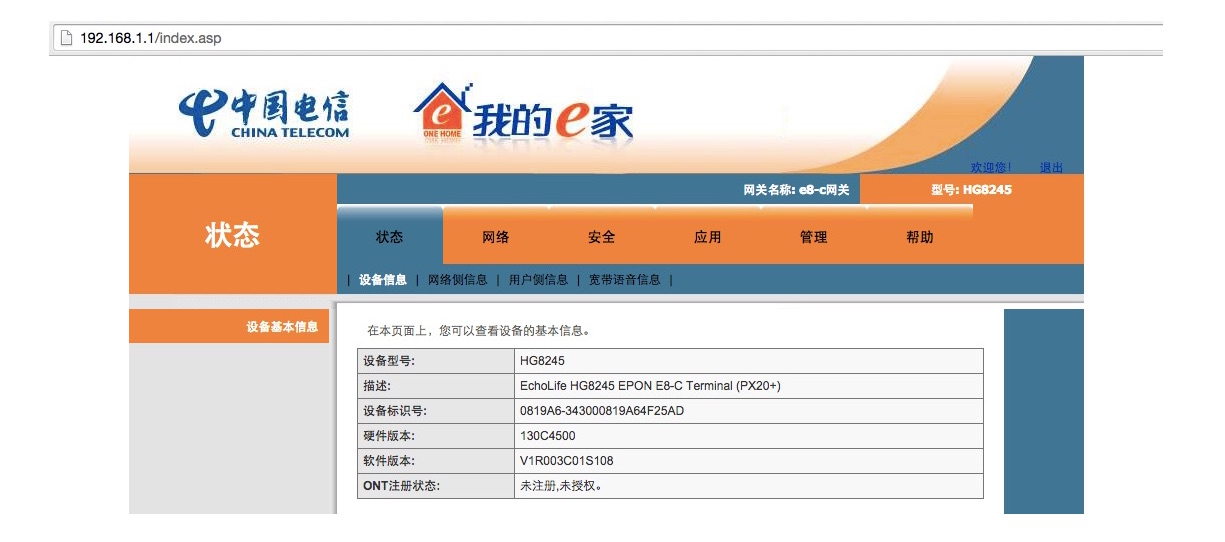
WAP(Dopra Linux) # When you login to web interface using useradmin, this is what you get:
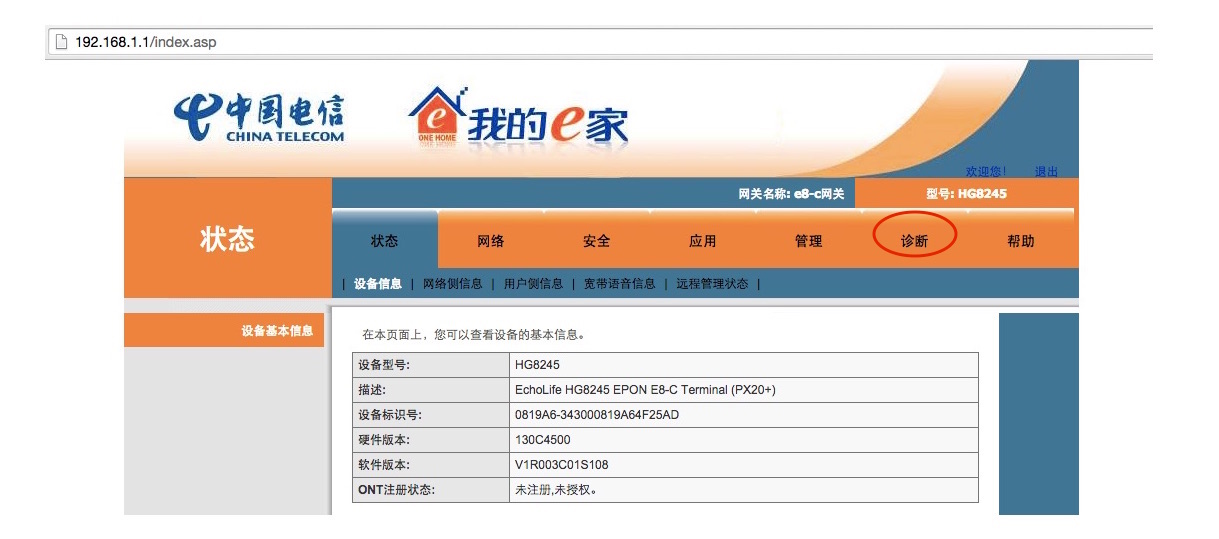
But when you login to web interface using telecomadmin, there is one additional menu showing up:

What if we try grep admin keyword? This is what you will get:
WAP(Dopra Linux) # grep admin /mnt/jffs2/hw_ctree.xml
<X_HW_WebUserInfoInstance InstanceID="1" UserName="useradmin" Password="ssn2q" UserLevel="1" Enable="1"/>
<X_HW_WebUserInfoInstance InstanceID="2" UserName="telecomadmin" Password="nE7jA%5m" UserLevel="0" Enable="1"/>
<X_HW_ServiceManage FtpEnable="0" FtpUserName="root" FtpPassword="admin" FtpPort="21" FtpRoorDir="/mnt/usb1_1/" FtpUserNum="0"/>
WAP(Dopra Linux) # It turned out that this ONT has a built-in FTP server running, with default root directory at /mnt/usb1_1. If you hook up a USB storage on its USB port, this ONT can be used as a file server, that can be accessed from anywhere. Cool stuff! But there is a little flaw in this system. The password cannot be changed!
Why don’t you try to copy hw_ctree.xml to a USB flash and analyze it further? I bet you would find a lot more hidden stuff in there. Let me know if you find anything interesting.
